The Dell™ Unified Server Configurator is a pre-installed configuration utility that enables systems and storage management tasks from an embedded environment throughout the server’s lifecycle.
Residing on an embedded flash memory card on the system board of supported servers, the Unified Server Configurator is similar to a BIOS utility in that it can be started during the POST (Power On Self Test) sequence and functions independently of the operating system (OS).
Using the Unified Server Configurator, you can quickly identify, download, and apply system updates without needing to search the Dell support site (support.dell.com). You can also deploy an OS with drivers (the USC stores Operating System drivers contained within a driver pack), configure a Redundant Array of Independent Disks (RAID), and run 32 -bit diagnostics to validate the system and attached hardware.
| NOTE: Certain platforms or servers may not support the full set of features provided by the Unified Server Configurator. |
Starting the Unified Server Configurator
To start the Unified Server Configurator, press the <F10> key within 10 seconds of the Dell logo being displayed during the system boot process.
The first time you boot the system, the Unified Server Configurator starts with the User Settings wizard displayed so that you can configure your preferred language and network settings.
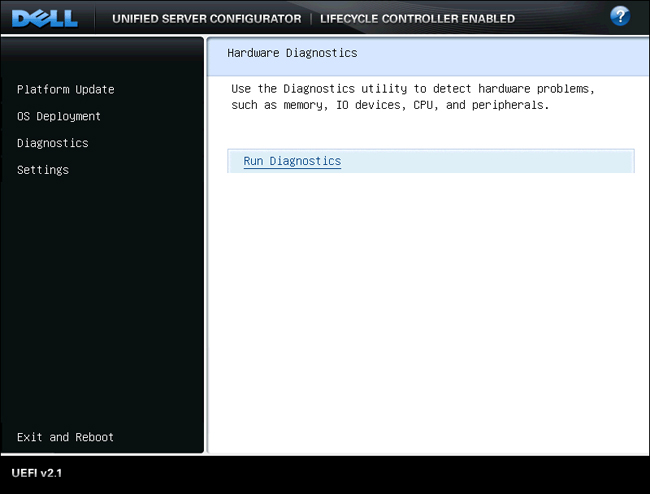
USC and Diagnostics
Dell has built into the Unified Server Configurator the ability to launch the system DMRK diagnostics.
| CE TIP: Learning about how the USC can be used to launch and utilize the DRMK diagnostics can be an advantage for you when addressing customer issues. Especially those that require diagnostics to be performed to identify the problem, as the diagnostics will always be on the system board, and there is no need to download them from support.dell.com, as long as the USC on the system is viable and functioning. |
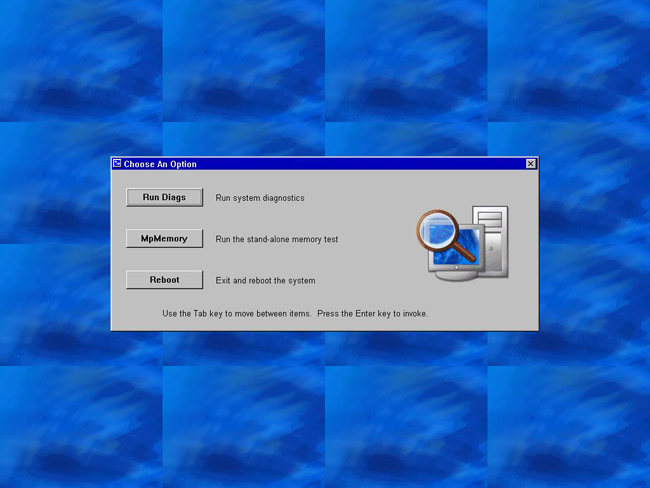
When launching the DRMK diagnostics please keep in mind the following:
- The BIOS provides “thunking” mechanism to allow DRMK DOS to run the tools.
- When the Diagnostics are complete a reboot of the system is required, sometime after initial launch a reboot will not be required.
The process below illustrates how to launch these diagnostics from the USC.
Platform Update using FTP Repository
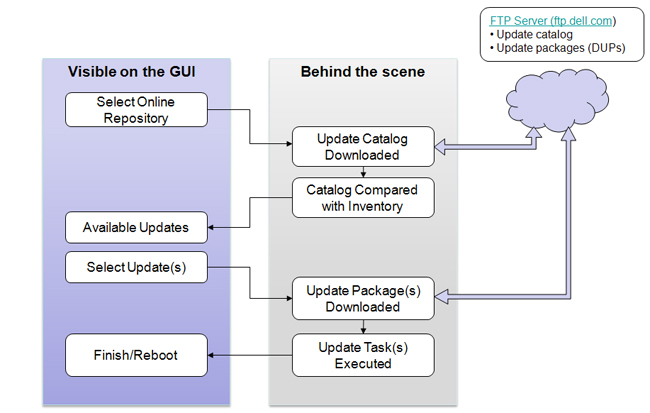
With the Unified Server Configurator Dell has provided the ability to update the USC platform, OS driver pack and system diagnostics using an FTP repository. By default the repository would be ftp.dell.com, but customers can create there own FTP repository and point to it for updates. The image below provides a high level overview of how the Platform Update works using an FTP repository.
The process below explains how to initiate a platform update using an FTP repository, like ftp.dell.com.
| Platform Update Using FTP Repository | |
| 1. | To perform the following procedure you need the following.
|
| 2. | Select the Platform Update option from the left menu of the Unified Server Configurator.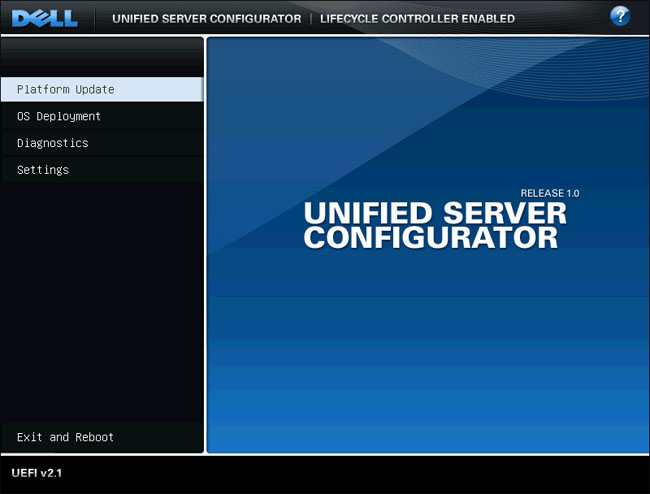 |
| 3. | On the next screen of the Platform Update Wizard, you will see a single option for Launch Platform Update, select this option.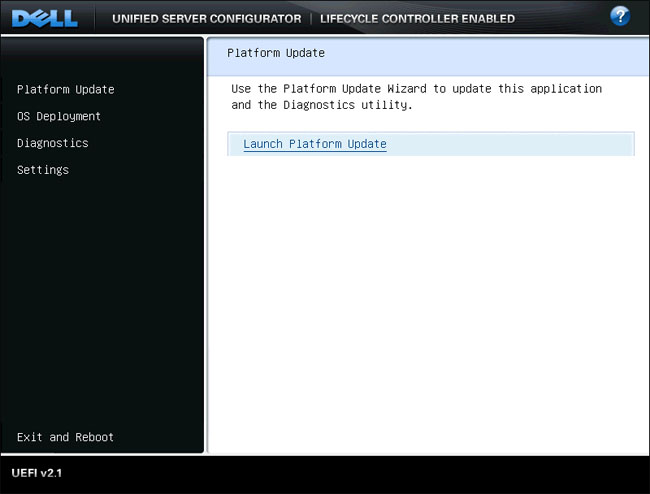 |
| 4. | This next screen select an FTP server or USB Key containing the Platform Update Repository files. Select FTP Server, and configure the FTP server address, proxy server information proxy port, proxy type, proxy user name and proxy user password information. Once all the information is populated click the next button to continue.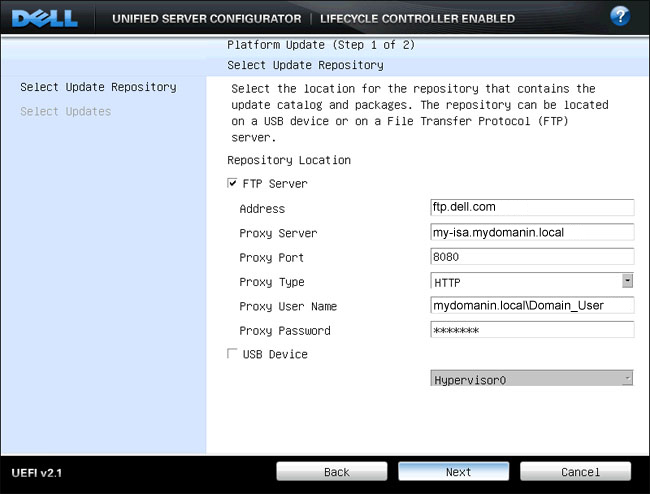 |
| 5. | The next screen in the platform updates wizard allows the user to select the available updates on the repository. Notice that this page shows the current version diagnostics, OS Drivers Pack and the USC platform version as well as the versions to be updated to during the update process.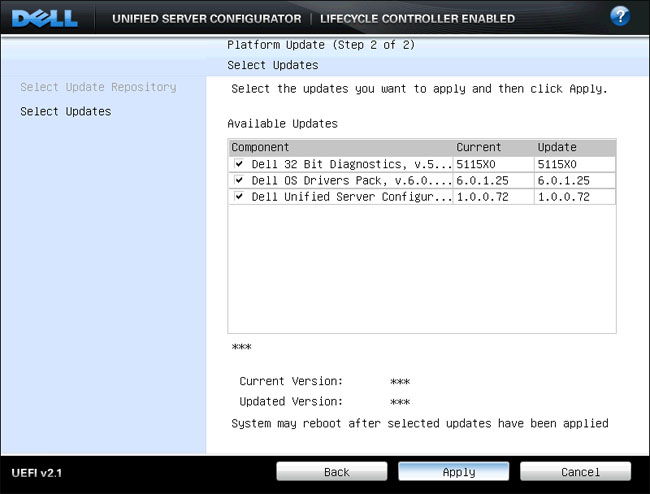 |
| 6. | Once the user sees this screen, the system is now performing the Platform Updates.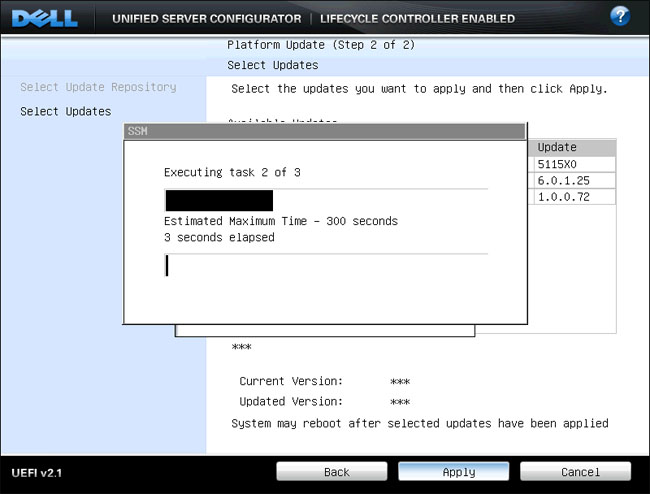 |
| 7. | Once the system completes each task for the update, the system will now reboot. You will notice on P.O.S.T. that the system will state it is entering system services, this is the normal and expected behavior.
|
| 8. | Once the system gets to the welcome screen of the USC after the first reboot, it will reboot again. However, upon the second reboot it will default to the normal boot process, as configured in the system BIOS. |
!!It is very important that you update the USC itself!!
Download this as a document: [wpdm_file id=”23″]