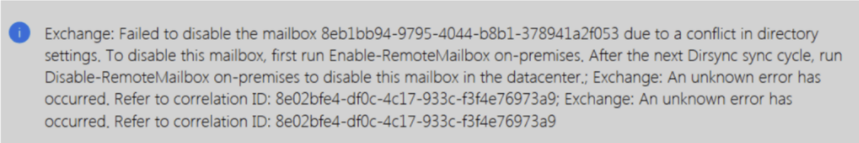
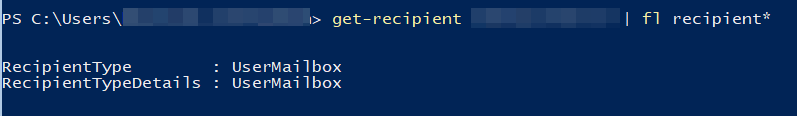
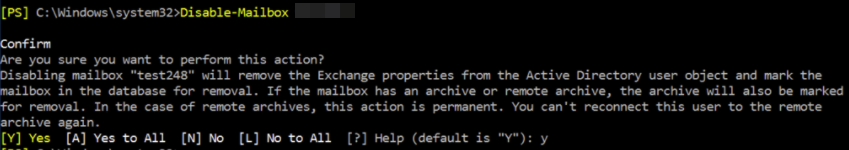
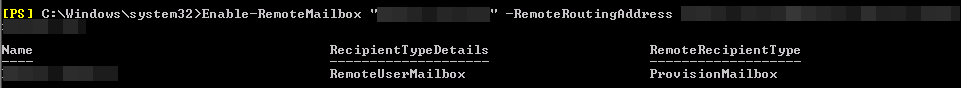
Self-service purchase gives users a chance to try out new technologies and develop solutions that ultimately benefit their larger organizations. Central procurement and IT teams have visibility to all users who buy and deploy self-service purchase solutions through the Microsoft 365 admin center. Admins can turn off self-service purchasing on a per product basis via PowerShell..
To read more about the Self-service purchase option, go to: Self-service purchase FAQ | Microsoft Docs
To disable the AllowSelfServicePurchase do the following:
#Install module
Install-Module -Name MSCommerce
#Import module
Import-Module -Name MSCommerce
#Connect
Connect-MSCommerce
#Get details
Get-MSCommerceProductPolicies -PolicyId AllowSelfServicePurchase
#Disable ProductID (or $True to enable)
Update-MSCommerceProductPolicy -PolicyId AllowSelfServicePurchase -ProductId CFQ7TTC0KP0N -Enabled $FalseThe following table shows the ProductID needed to enable or disable
| Product | ProductId |
|---|---|
| Power Apps per user | CFQ7TTC0KP0P |
| Power Automate per user | CFQ7TTC0KP0N |
| Power Automate RPA | CFQ7TTC0KXG6 |
| Power BI Premium (standalone) | CFQ7TTC0KXG7 |
| Power BI Pro | CFQ7TTC0L3PB |
| Project Plan 1 | CFQ7TTC0KXND |
| Project Plan 3 | CFQ7TTC0KXNC |
| Visio Plan 1 | CFQ7TTC0KXN9 |
| Visio Plan 2 | CFQ7TTC0KXN8 |
source: Use AllowSelfServicePurchase for the MSCommerce PowerShell module | Microsoft Docs